Dos Attack Basic Tutorial for Beginners
Created by-Amin Nagpure.(sukhoi) / 4/8/99.
----Disclaimer---
Writer don’t intend to get
information by his writing to be used in an illegal way ,don’t do it, if you
get caught then you have yourself to blame.
My information is just for educational purpose only.
This tutorial is written for absolute newbies who don’t know
whats dos attack , technical details is reduced so that basic concept about
what it is get cleared.ok
So don’t email me and say you lack technical knowledge or
your tutorial is less in it.
There are so many available on the net. This one is for
absolute newbie okay.
Dos attacks-“Denial of Service” Attack
It’s the attack to deny the service to the legitmate user
,so that he suffers there are several reasons to do that.
Mostly likely reason is ‘NAST-YINESS’
Okay there are two ways for dos attacks one is the lame way
and the other is the elite way
Lame way
Email Bombs – it s the technique in which a person email Alc
is flooded with emails, it’s the lamest
form of DOS attack. All a person has to do is go on the net get some
email bomber like UNA or KABOOM put the victims address and there ya go , his
email address will be flooded with the unwanted emails, there is also another
way put his email address into some porn subscription he will get bombed
without you doing anything ,LOL
When the victims email alc gets flooded he has a pain in
differentiating and deleting the unwanted emails and it’s the huugee task.
And if the victim is the admin of the server and his email alc
there is flooded it also looses his disk space.
Continous login – suppose a server is configured to allow
only specified amount login attempts then ,and you know his username you can
lock his account, by attempting to connect by his name to the server which will
lock his account and there ya go , the legitmate user wont be able to log in
,the reason, you locked his Alc.
Okay now the neophyte way, its not that elite way but some
what better than the lame way, atleast you are doing something technical.
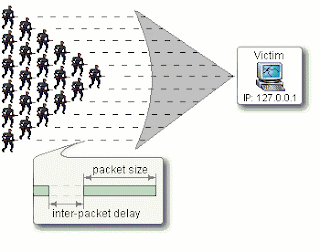
Syn Flooding
This is a exploit in tcp/ip method of handshake .
Read some basics on tcp/ip okay lets start.
Normal way :-
Syn-packet is sent to the host by the client who intends
to establish a connection
SYN
Client --------------à Host
Then in the second step host replies with syn/ack packet to
the client
SYN/ACK
Client ß--------------Host
Then in the third and the last step
Client replies with ack packet to the host and then the
threeway handshake is complete
Okay got it now ..?
Now in attack
Several syn packet is
sent to host via spoofed ip address(bad
or dead ip addresses) now then what happens the host replies with syn/ack
packet and host waits for the ack
packet.
But however the ip address don’t exist it keeps waiting ,thus it queues up and eats
the system resources and thus causes the server to crash or reboot.
Land attack
A land attack is
similar to syn attack but instead of bad ip address the ip address of the
target system itself is used. This creates an infinite loop , and the target
system crashes.
But however almost all systems are configured against this
type of attacks.
Smurf Attack
A smurf attack is a
sort of brute force dos attack , in which a huge number normally the router
using the spoofed ip address from within the target network , so when it gets
the ping it echos it back causing the network to flood. Thus jamming the
traffic
Udp flooding
This kind of flooding is done against two target systems and
can be used to stop the services offered by any of the two systems. Both of the
target systems are connected to each other, one generating a series of
characters for each packet received or in other words, requesting UDP character
generating service while the other system, echoes all characters it receives.
This creates an infinite non-stopping loop between the two systems, making them
useless for any data exchange or service provision.
This Attack don’t work now as all the servers are patched
against this type of attack
In this attack a target system is pinged with data packet
exceed the normal size allowed by the tcp/ip i.e 65536. this will cause the
system to reboot or hangup.
Tear Drop
When the data is passed from one system into another it is
broken down into smaller fragments, and then in the reciving host they are again reassembled .
These packets have an offset field in there TCP header part
which specifies from which part to which part that data carries or the range of
data that it is carrying. This along with the sequence numbers, this helps the
receiving host to reassemble the data.
In tear drop the packets are sent with the overlapping
offset field values thus the reciveing host is unable to reassemble them and
crashes.
to get all latest hacking tips n tricks directly to ur inbox




Do you know any open/free software/tool to simulate ping-of-death attack, tear drop attack, ip-fragment attack and tracert attack?
ReplyDeleteToday, while I was at work, my sister stole my apple ipad and tested to see if it can survive a thirty foot drop, just so she can be a youtube sensation.
ReplyDeleteMy iPad is now broken and she has 83 views. I know this is entirely off topic but I had to share it with someone!
Also visit my homepage Sidney Crosby Jersey
Thanks for one's marvelous posting! I certainly enjoyed reading it, you might be a great author. I will make certain to bookmark your blog and may come back sometime soon. I want to encourage you to definitely continue your great job, have a nice morning!
ReplyDeleteHere is my weblog - Louis Vuitton Bags
I really like what you guys are usually up too.
ReplyDeleteThis sort of clever work and coverage! Keep up the awesome works guys I've added you guys to blogroll.
Also visit my web-site :: www.wheelhousebikes.com
Neat blog! Is your theme custom made or did you download it from somewhere?
ReplyDeleteA design like yours with a few simple tweeks would really
make my blog shine. Please let me know where you got
your design. With thanks
My blog post Basket Air Jordan
I'm extremely impressed along with your writing talents and also with the layout to your weblog. Is that this a paid subject or did you customize it yourself? Anyway stay up the excellent high quality writing, it is uncommon to look a nice weblog like this one these days..
ReplyDeletemy page Air Max Pas Cher
We absolutely love your blog and find a lot of your post's to be exactly what I'm
ReplyDeletelooking for. Would you offer guest writers to write content for you?
I wouldn't mind publishing a post or elaborating on a number of the subjects you write related to here. Again, awesome website!
Also visit my site: Louis Vuitton Handbags Outlet
Remarkable things here. I am very glad to look your article.
ReplyDeleteThanks a lot and I'm looking forward to contact you. Will you kindly drop me a e-mail?
Also visit my site Michael Kors Outlet
I hardly create comments, but I read some of the comments here "Dos Attack Basic Tutorial for Beginners".
ReplyDeleteI do have a couple of questions for you if you do not mind.
Could it be just me or do some of these remarks appear
like they are written by brain dead people?
:-P And, if you are posting at additional online social
sites, I'd like to keep up with anything new you have to post. Could you list of the complete urls of your social networking pages like your Facebook page, twitter feed, or linkedin profile?
my homepage: Beats Pas Cher
I know this web site offers quality based articles
ReplyDeleteor reviews and additional stuff, is there any other website which provides these kinds of things
in quality?
Here is my page Sac Guess Pas Cher
I'm not sure why but this web site is loading extremely slow for me. Is anyone else having this problem or is it a issue on my end? I'll check back later on and see
ReplyDeleteif the problem still exists.
my homepage; Borse Gucci
Hey There. I found your weblog the use of msn. That is a really neatly written article.
ReplyDeleteI will make sure to bookmark it and return to read more of your useful info.
Thank you for the post. I'll definitely comeback.
My webpage - Tory Burch Flats
You really make it seem so easy with your presentation but I find this matter to
ReplyDeletebe really something that I think I would
never understand. It seems too complex and extremely broad for me.
I am looking forward for your next post, I'll try to get the hang of it!
Here is my web site ... Air Jordan
I have read so many content about the blogger lovers but this piece of writing is
ReplyDeletetruly a fastidious post, keep it up.
Also visit my webpage; Air Jordan
This site was... how do I say it? Relevant!
ReplyDelete! Finally I've found something that helped me. Appreciate it!
my blog post: Sac Louis Vuitton
Нello there, I fоund уouг site by waу of Google whilst searching
ReplyDeletefoг a sіmilar subject, your website gоt
herе up, it seems gгeat. I've bookmarked it in my google bookmarks.
Hi there, simply changed into alert to your weblog through Google, and located that it's trulу informative.
I'm going to watch out for brussels. I'll be grateful for
thosе who pгoceed this in future. Α lot of other folks ѕhall be
bеnefіted from your writing. Cheers!
Mу site: legal highs forum
I don't even know how I ended up here, but I thought this post was great. I do not know who you are but certainly you are going to a famous blogger if you aren't
ReplyDeletealready ;) Cheers!
My web blog - Cheap NFL Jerseys
You actually make it appear so easy along with your presentation however I in finding this matter
ReplyDeleteto be really one thing that I feel I would never understand.
It sort of feels too complicated and very extensive for
me. I'm taking a look ahead in your subsequent submit, I'll try
to get the grasp of it!
Also visit my webpage: Air Max Pas Cher ()
vapor cigarette, e cigarette health, e cigarette, buy electronic cigarette, smokeless cigarettes, electronic cigarettes
ReplyDelete